Same Origin Policy (SOP) - Lab 4
Intro
In Lab 2 & 3, we have seen that same origin policy (SOP) allows embedding resources but not reading them.
In this lab we are going to see that SOP also allows writing (sending) requests.
Without further talk, let’s get started 🚀
⚡ Lab 4 : cross-origin write : allowed
-
Setup a quick domain in requestcatcher. It is a simple public HTTPs listener (webhook).
-
While you are reading this page. Open browser Console
-
Paste the following JS snippet, replace
AAAAAAAAAAAAAAAAAAwith your domain that you made in step 1.
url = "https://AAAAAAAAAAAAAAAAAA.requestcatcher.com/admin "
fetch(url,{method: 'POST', body: "yaaay!"}).then(response =>
response.text()).then(function (data) {
console.log(data)
});
- This snippet is going to make HTTP POST to a dummy endpoint /admin with
payload “
yaaay!”. Hit enter to fire up the request.
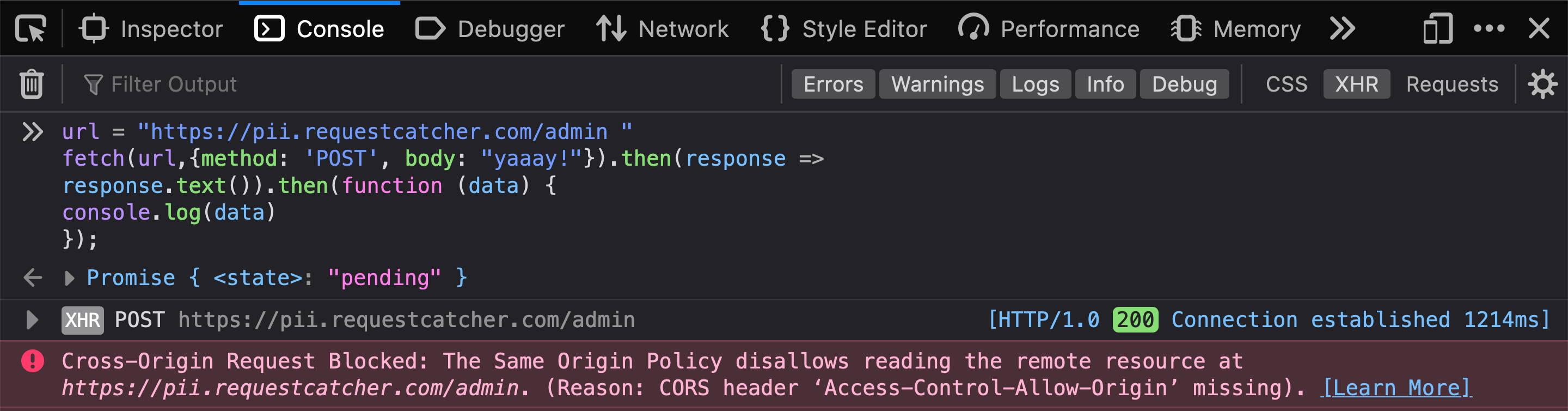
-
You should see that we were able to successfully make the request.
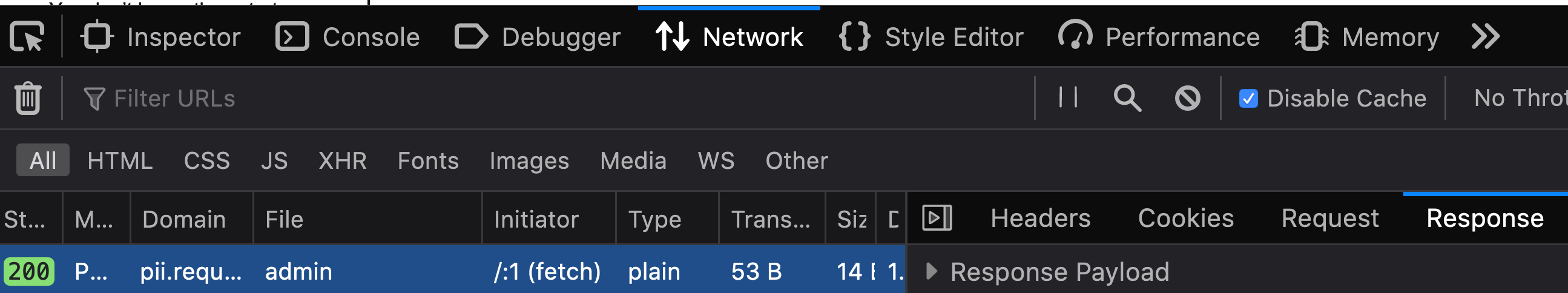
Figure 2 shows that we get
200 status codefrom the server. The warning in the console is about blocking reading the content of the response (as we explained in lab 3).
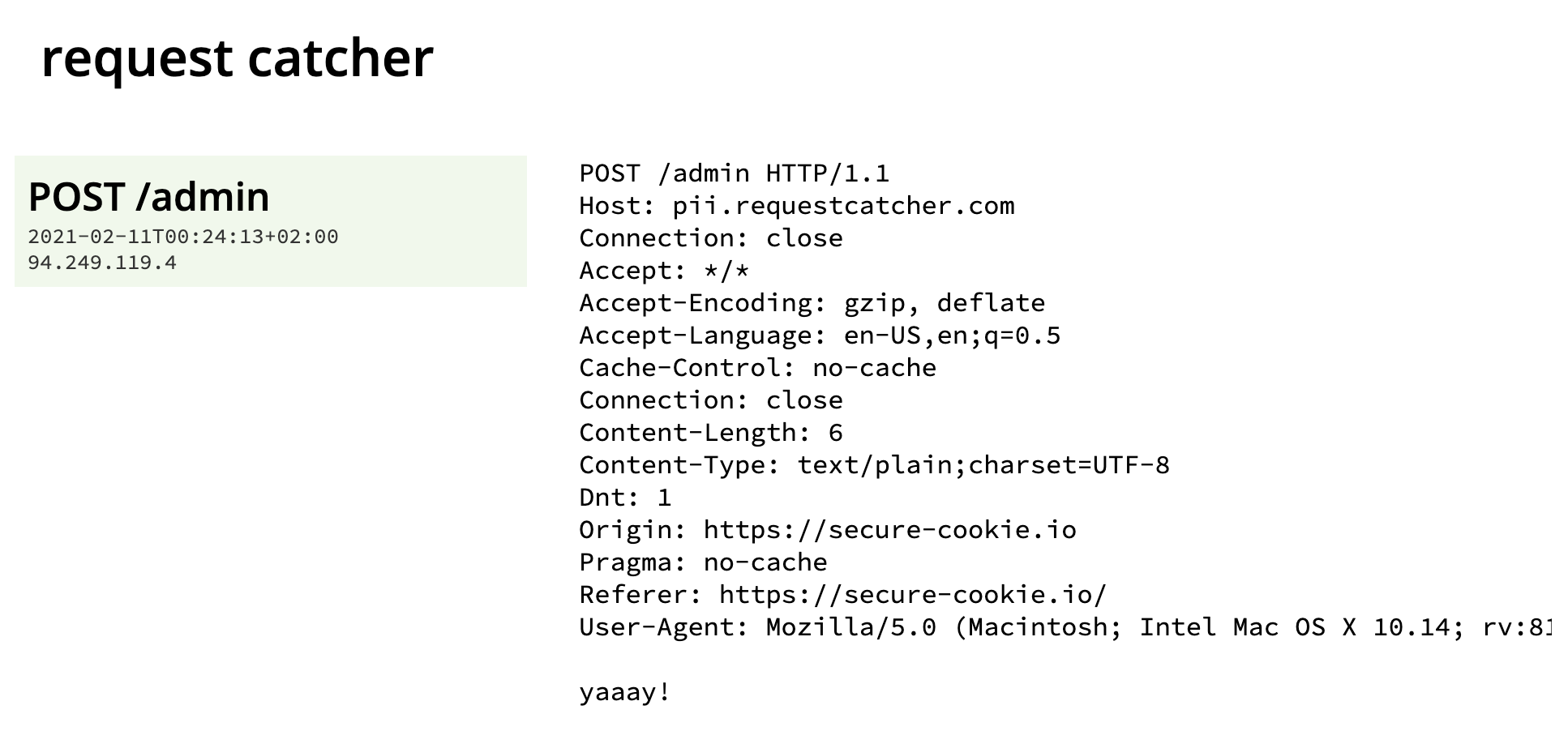
- Going to the requested endpoint, we can see that it got our request and the payload.
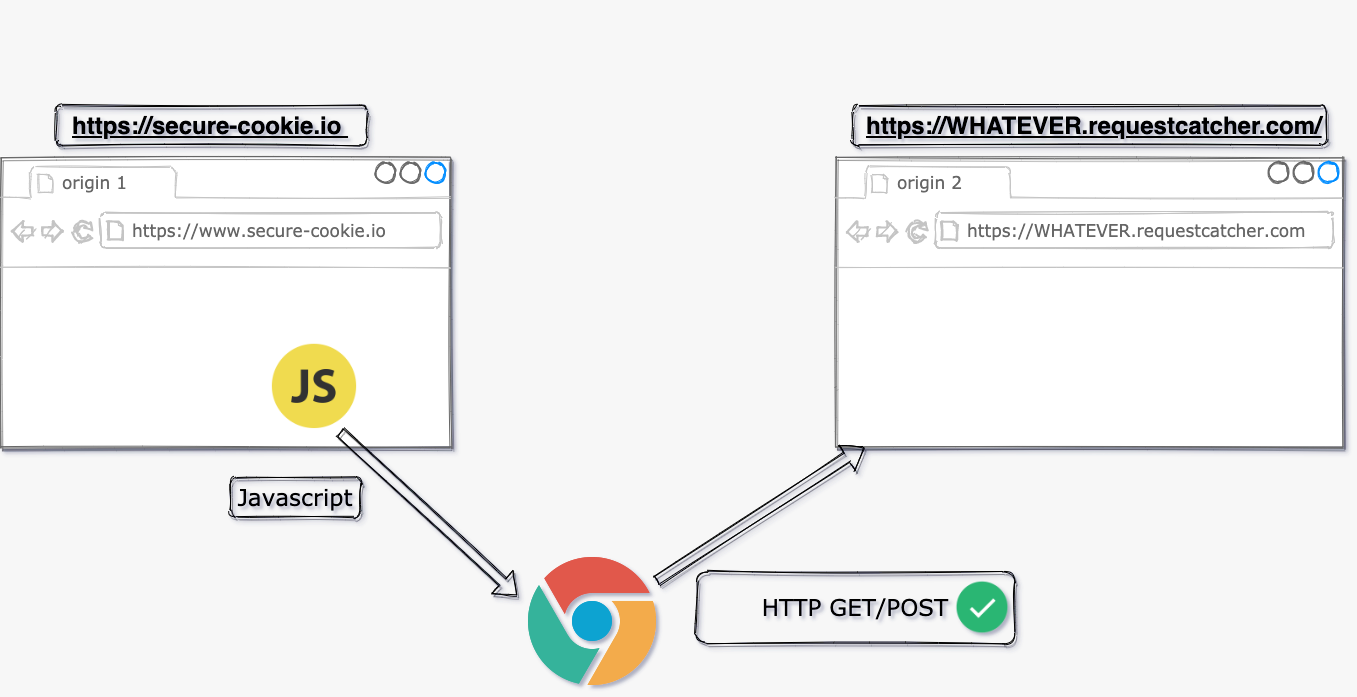
We can conclude, that same origin policy allowed a JS from origin
https://secure-cookie.io
to write HTTP request cross-origin to
https://WHATEVER.requestcatcher.com/
Why is this important❓
There’s a big misconception that same origin policy and CORS can protect against CSRF attacks.
In CSRF, attacker can make HTTP calls on victim’s behalf. Understanding that the forged request by the attacker will hit the endpoint is quite important.
What if the requestcatcher origin was actually
https://transfer.your-bank.com/sendMoney
Then an attacker can forge a JS similar to the one that we did before, and instead of sending “yaaay!”, the attacker would transfer money to his/her account.
That would be a successful CSRF attack, because the request will hit the endpoint successfully. The attacker can NOT read the response from the endpoint due to SOP, but that doesn’t matter anymore as the endpoint got the request and will process the payment.
Check out CSRF lab to better know how CSRF attack works 🔥.
